CCSP Domain 4 - Secure SDLC Process MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help you pass the CCSP exam. We’re going to review some of the major topics related to secure software development in Domain 4. By the end, you will understand the linkages, which should help you with your studies.

This is the second of seven videos for Domain 4. I have included links to the other MindMap videos in the description below. These MindMaps are just a small part of our complete CCSP MasterClass.
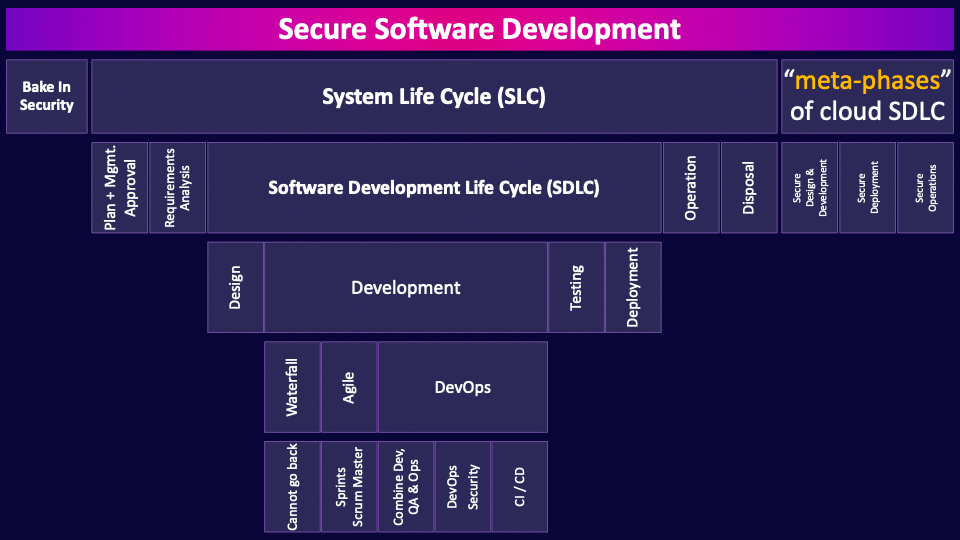
Secure Software Development
Secure software development, as the name implies, is all about how we integrate security into the software development process. It is incredibly important for security to be involved right from the start and throughout the entire system life cycle so that applications provide the required confidentiality, integrity, and availability.
Sadly, security requirements are typically labeled as non-functional requirements, and when a development project is inevitably over budget and behind schedule, what are the first things management cuts? Non-functional requirements. Who needs those anyways?
Bake In Security
When should security become involved in any development project?
Right from the very start and throughout the whole process. This is the concept of baking security in. It is significantly more expensive to try and retrofit and add security later vs. building it in from the start.
System Life Cycle (SLC)
Let’s define the system life cycle, the SLC, which is the overall life of a system from cradle to grave, and it encompasses the software development life cycle–the SDLC. The SLC includes planning, designing, development, testing, operations, maintenance and eventual disposal of the system.
Plan & Management Approval
Starting with defining a plan for a project, what goals and objectives will this project help the organization achieve? What are the high-level cost estimates? You will also need to obtain management approval to proceed with the requirements analysis.
Requirements Analysis
The requirements analysis phase is where business requirements (user needs, the business uses of the system, as well as the type of data to be collected, stored, and processed) are gathered and validated to create a detailed set of requirements.
Software Development Life Cycle (SDLC)
The software development life cycle (SDLC), as the name implies, focuses on the development phases.
Design
The design phase involves translating requirements into a detailed design plan
Development
The development phase is where the coding begins–writing code to create the system. There are many methodologies that have been developed over the years to guide the development process and I’ll cover just a few key ones:
Waterfall
Waterfall begins with a plan, then defining requirements, building, testing and finally releasing.
Cannot go back
The defining characteristic of waterfall is that each of these phases are conducted one after another and you cannot go backwards. Water can only flow downhill. So, if you discover as part of a two-year waterfall project that you missed a requirement, you can’t go back and re-define the requirements. You must proceed through build, test and release, and then include the missed requirement as part of the next waterfall cycle.
Agile
Agile was created to address this problem.
Sprints
Agile follows exactly the same phases as waterfall, but does them in, typically, two-week sprints. Rapidly iterating through plan, define, build, test and release. Waterfall is better suited for projects where no changes are planned, and agile is better for projects where many changes are expected, where organizations want to rapidly iterate ideas and fail fast through rapid sprints.
Scrum Master
Agile includes the role of a scrum master. This person is a facilitator, and I am intentionally emphasizing that word, facilitator. A scrum master has no real authority over the team, they are not project managers, but rather there to act as a coach to the team and facilitate communications with the organization to maximize the productivity of the team.
DevOps
And of course, the latest, and debatably greatest, software development methodology is DevOps. This is what all the cool kids are doing.
Combine Dev, QA & Ops
DevOps, as the name implies, combines development (the Dev part), quality assessment and operations (the Ops part) to significantly shorten the development lifecycle, possibly to the point of releasing new code daily. DevOps includes automated practices such as continuous integration and continuous delivery.
DevOps Security
The DevOps approach can seem contradictory to the practice of having security built into the development process. This is because sacred security practices like segregation of duties between development and operations are intentionally removed. Many other traditional security techniques are too slow to fit into the rapid iterations of DevOps. Therefore, integrating security into DevOps requires strong engagement between developers and security, using secure development frameworks, automating much of the security testing, and only using traditional security testing techniques, such as penetration testing, sparingly.
CI / CD
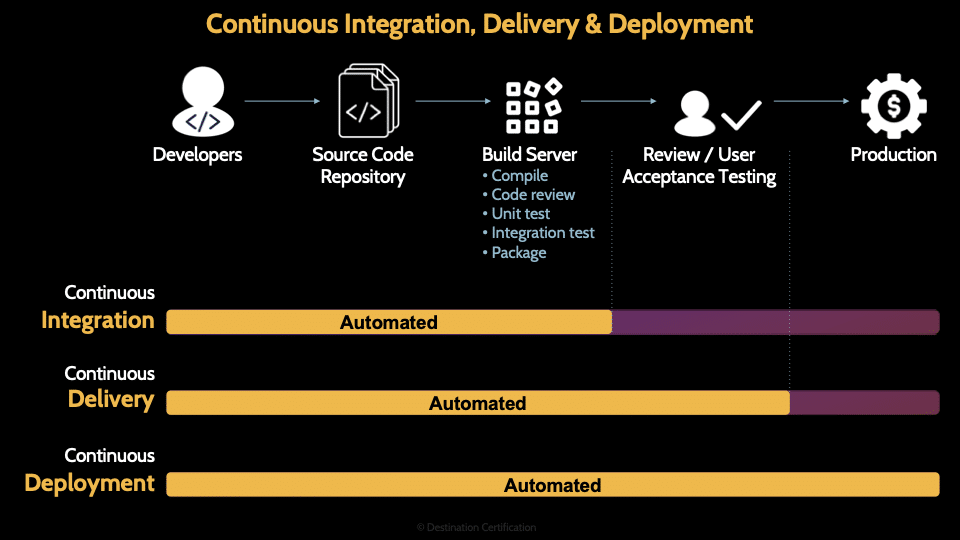
CI/CD stands for continuous integration, continuous delivery (or continuous deployment–more on that in a moment). CI/CD is an approach that uses a lot of automation to speed up software delivery. Code is automatically committed to a repository, and then building and testing is automatically performed, and even pushing code into production can be automated.

You can see here that continuous integration means automating the upload of code to a repository, committing that code, and running it through the build server to compile the code and run a bunch of automated tests.
There are two versions of CD:
- Continuous Delivery automates the review/user acceptance testing, but there is still a manual step required to move code into production.
- Continuous Deployment automates everything including automatically moving code into production after all the testing has passed successfully.
Testing
It is very important to test throughout the system lifecycle from validating business requirements, reviewing designs, testing units, interfaces, integration and whole software systems during development and operations.
Deployment
Deployment is the final stage of the software development life cycle, and deployment is where a system is moved into production.
Operation
Operations is where the system is being actively used for business purposes. It is in operation.
Disposal
The disposal phase is extremely important and often overlooked. When a system is retired and replaced there needs to be controls in place to ensure data, logic, processes, etc. are migrated to the new system with integrity. Data in the old system is retained as necessary, and if the old system and data are to be deleted, the data may need to be defensibly destroyed, and not just left on a hard drive that is sold on eBay. Hurray for privacy breaches.
“meta-phases” of cloud SDLC
For the final part of this MindMap, the Cloud Security Alliance created three metaphases to describe the software development lifecycle. I’ll be honest, I’ve never come across these in the real world, but I know they are on the exam, so let’s cover them:
Secure Design & Development
Secure design and development is a phase that includes everything from training and developing organization-wide standards to actually writing and testing code.
Secure Deployment
Secure deployment includes security and testing activities when moving code from an isolated development environment into production.
Secure Operations
The third and final meta-phase, secure operations, includes securing and maintaining production applications, including external defenses such as web application firewalls and ongoing vulnerability assessments.

That’s all for our overview of secure software development within Domain 4, covering the most critical concepts you need to know for the exam.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!