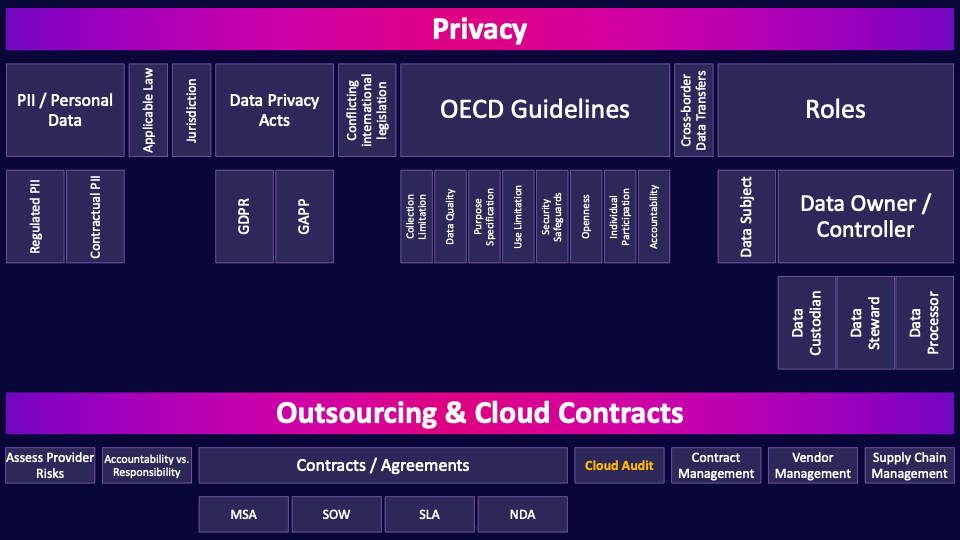
CCSP Domain 6 - Operational Controls MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
This is our first MindMap for Domain 6, and we're going to be discussing Privacy, Outsourcing & Cloud Contracts. Throughout this MindMap, we will be explaining how these ideas interrelate to help guide your studies. This MindMap is just a small fraction of our complete CCSP MasterClass.

This is the first of two videos for Domain 6. I have included links to the other MindMap videos in the description below. These MindMaps are a small part of our complete CCSP MasterClass.
Privacy
Let’s begin with a definition of privacy. It is the state or condition of being free from being observed or disturbed by other people. You should remember that exact definition for the exam. But what does it mean? Being free from being observed and disturbed. Essentially, privacy is the idea that an individual can withhold parts of their personal information from wider society. To control what personal information others know about them, as their personal information can potentially be used against them in ways that would disturb them: limit what jobs they can get, where they can travel, whether they can get health insurance, etc.
PII / Personal Data
The major thing that we are protecting from a privacy perspective is personal data which can be defined as information that can be used on its own or in combination to identify an individual.
Regulated PII
There are two types of personal data or personally identifiable information–PII– that you need to know about. The first is regulated PII, which is personal information that must be safeguarded according to a specific regulatory regime, such as the GDPR.
Contractual PII
The other type is contractual PII, which is personal information that must be protected according to contractual agreements. As an example, your company may be processing personal data on the behalf of another organization. You must abide by any safeguards that were set out in the contract.
Applicable Law
Applicable law refers to the specific set of laws or legal standards that govern a particular case or contract. This determines which rules, statutes, or regulations are used to interpret legal obligations and rights. For instance, a contract might specify that California law applies, meaning California's legal codes will be used to resolve any disputes related to that contract.
Jurisdiction
Jurisdiction refers to the authority of a particular court or legal body to hear and decide a case. It’s about "where" or "who" has the power to enforce or interpret the applicable law. For example, a court in British Columbia may have jurisdiction over a case involving parties within its geographic area, even if the applicable law is from another state or country.
Data Privacy Acts
Many jurisdictions throughout the world have their own data privacy acts. Organizations must abide by the applicable legislation–which can be complicated to figure out–so talk to a lawyer!
GDPR
There are loads of different privacy laws and regulations around the world, and I’m happy to report that you do not need to be an expert on all of them for the CCSP exam. However, you should know a wee bit about the GDPR, the General Data Protection Regulation, which is the core of the European Union’s digital privacy legislation. The GDPR is an extremely important regulation as it is one of the most stringent in the world, and many countries around the world model their privacy regulations on the GDPR. It is very much the global bellwether for privacy.
GAPP
The Generally Accepted Privacy Principles –GAPP– was renamed the Privacy management Framework –PMF–in 2020. The PMF aims to help organizations create privacy programs that can bring about opportunities while mitigating risks and addressing obligations.
Conflicting international legislation
In some cases, sets of international legislation may come in conflict with each other, which can present organizations with complex legal challenges. One example is the US CLOUD Act and the EU’s GDPR. As long as certain conditions are met, a warrant under the US CLOUD Act allows American authorities to compel the recipient to disclose data, no matter where it is stored. If this data is stored by an EU-based subsidiary and includes information on EU residents, disclosing the data could be in breach of the GDPR. In these kinds of complicated scenarios, you will need to find experienced legal counsel to help you resolve these conflicts. So again, talk to a lawyer.
OECD Guidelines
The Organisation for Economic Co-operation and Development, the OECD, have come up with a set of privacy guidelines or principles. I’m emphasizing the word guidelines, because guidelines are not mandatory, they are best practices or suggestions. This is very much true of the OECD Privacy Principles; they are not mandatory requirements that an organization must meet, but rather they provide best practices and the basis for the creation of leading privacy programs within an organization. They help organizations structure their privacy program and consider what the program should cover. Eight privacy principles are defined in the OECD Guidelines.
Collection Limitation
The first is collection limitation, which means that organizations should limit the collection of PII, obtain it lawfully, and where appropriate, with the knowledge or consent of the data subject. The data subject being the individual for whom the data is about.
Data Quality
The data quality principle means PII should be relevant, accurate, complete and kept up-to-date. In other words if an organization collects PII they are now accountable for the integrity and accuracy of the data.
Purpose Specification
The purpose specification principle means the purposes for which PII is collected should be specified when collected. Organizations should clearly articulate what the PII they collect will be used for.
Use Limitation
The use limitation principle means PII should only be used or disclosed based on the purposes for which it was collected with consent of the data subject or by authority of law.
Security Safeguards
Security safeguards means PII should be protected by reasonable security controls against loss, unauthorized access, destruction, use, modification, etc. Basically, good security controls need to be in place to protect the PII.
Openness
The openness principle relates to an organization's culture. There should be a general policy of openness about developments, practices and policies with respect to PII. Organizations should not hide or be sketchy about what they are collecting and using PII for.
Individual Participation
The individual participation principle means an individual, a data subject, should have the right to obtain their data from the controller, and have their data removed. Under GDPR this is often referred to as the right be forgotten
Accountability
And the last principle, accountability, means a data controller should be accountable for complying with the other principles. In other words, there must be an owner, a data controller, who has clear accountability for the protection of PII.
Cross-border Data Transfers
Some jurisdictions, such as the European Union, have restrictions on how personal data can be transferred outside of their borders. You need to be aware of this legislation before you make any transfers, otherwise you might have a regulatory violation on your hands. This is an especially easy trap to fall into in the cloud, because it’s so easy to accidentally store or transfer data to other countries around the world.
Roles
There are a range of roles that you need to understand in the cloud. It’s important to note who is accountable and who is responsible for what.
Data Subject
The data subject is the individual to whom any personal data relates. It is data about them.
Data Owner / Controller
The data owner, also known as the data controller, is the most important role, as the owner is accountable for the protection of the data. The owner will define the classification for data and the owner is then accountable for ensuring the data is protected accordingly.
Data Custodian
Data custodians have technical responsibility for the data. This means that custodians are responsible for things like ensuring data security, availability, and capacity, as well as that backups are performed and that data can be restored. They are responsible for the technical aspects of data.
Data Steward
Data stewards, on the other hand, have a business responsibility for the data. Meaning stewards are responsible for ensuring data governance, data quality, compliance. Essentially, stewards are employees from the business who are responsible for ensuring the data is useful for business purposes.
Data Processor
Data processors, as the name implies, are responsible for processing data on behalf of the owners. A typical example of a data processor is a cloud service provider–they are storing and processing data on behalf of the owner.
Outsourcing & Cloud Contracts
Okay, moving on to the next major section of this MindMap–outsourcing & contracts. Your organization is likely reliant on a bunch of different cloud service providers. This outsourcing helps your company focus on what it does best, but it also means that you are going to have to rely on a bunch of other parties in order to keep the gears turning. We use contracts to ensure that vendors live up to their promises.
Assess Provider Risks
Before anyone signs a contract, it’s important to assess the risks from each individual provider. Whenever you outsource something, you are ceding a degree of control. You need to do a thorough risk assessment to ensure that the provider can meet your requirements, and that it will be a trustworthy partner throughout the business relationship.
Accountability vs. Responsibility
We’ve discussed accountability and responsibility a bunch of times now in these MindMaps–primarily in the first MindMap of Domain 1.
What bears repeating is that ultimately the customer remains accountable for the security of their data. The customer cannot outsource the accountability for protecting their data, but they can delegate the responsibility.
Contracts / Agreements
Contracts are essential for cloud services because they define and protect the rights, responsibilities, and expectations of both the service provider and the customer. Cloud service contracts serve as a legal foundation for the relationship and address critical aspects such as data security, service levels, liability, and compliance, among others.
MSA
An MSA is a master service agreement. If we want to build a long term legal relationship with a provider, we will often set up an MSA that defines the basics of the relationship, such as definitions, dispute resolution, and contract termination clauses.
SOW
If we establish an MSA, we can then create statements of work –SOWs–as contracts on a per project basis. By having an MSA outlining the relationship, it can help to reduce some of the legal costs associated with each individual project, while still allowing flexibility for each project.
SLA
One important contractual tool that a cloud consumer can use to communicate their requirements to a cloud provider are SLAs, service-level agreements. SLAs are documented commitments by the service provider to a consumer covering things like confidentiality, integrity, availability, responsiveness, and so forth. SLAs are addendums to the overall contract.
NDA
An NDA is a non-disclosure agreement. When signing up with certain services, you may be forbidden from disclosing certain information about the service or the relationship.
Cloud Audit
As a cloud customer you generally aren’t able to audit your provider yourself. Most of the big cloud providers will not provide a right to audit. Instead, you’ll have to rely on third party audits to hopefully provide you with the assurance you’re looking for.
Contract Management
Contract management is important for ensuring that both the provider and the consumer fullfill their duties. Contract management can involve a range of stakeholders throughout the customer organization, including legal, IT security, finance, compliance, operations and leadership.
Contract management involves reviewing initial contracts to ensure that it includes key requirements, as well as monitoring the contract throughout the relationship to ensure that provisions are being met. If there are disputes, you may need to pursue arbitration or terminate the contract.
Vendor Management
Vendor management is a process that involves:
- Defining business goals and requirements
- Choosing the best provider
- Monitoring performance
- And consistently meeting goals
Security must be involved right from the start of the process and throughout the relationship.
Supply Chain Management
Cloud services are really just another part of your organization’s supply chain. Like all other supply chains, you must manage it carefully. Two important standards for supply chain management include:
- ISO 28000, which is a specification for security management systems for the supply chain.
- ISO 27036, which is a standard that delves into information security for supplier relationships. Part 4 is especially important, because it discusses guidelines for the security of cloud services.

That’s it for our overview of privacy, outsourcing and cloud contracts within Domain 6, covering the most critical concepts you need to know for the exam.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!