CCSP Domain 4 - Identity and Access MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
This is our seventh and final MindMap for Domain 4, and we're going to be discussing Access Control. Throughout this MindMap, we will be explaining how these ideas interrelate to help guide your studies. This MindMap is just a small fraction of our complete CCSP MasterClass.

This is the seventh of seven videos for Domain 4. I have included links to the other MindMap videos in the description below. These MindMaps are a pint-sized part of our complete CCSP MasterClass.
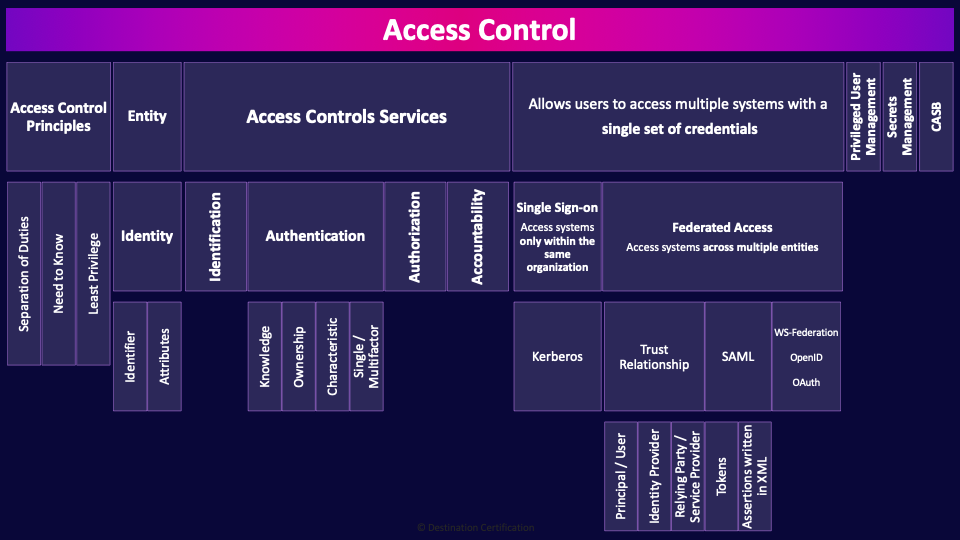
Access Control
Access controls are the collection of mechanisms that work together to protect access to the assets of an organization. These access controls can be both physical controls, like locks, and logical controls, such as a login mechanism to access an operating system.
Access controls enable management to:
- Specify which users
- Can access which resources
- Which operations they can perform
- And provide individual accountability
Access Control Principles
There are three major principles that we apply throughout access control.
Separation of Duties
The first is Separation of Duties. To divide up key processes into multiple parts assigned to different people.
Need to Know
Need to know and least privilege are very similar–only give users the access they need based on their job, and nothing more. But there is a subtle difference between them that you must understand. Need to know is focused on restricting a user’s knowledge (access to data) to only the data required for them to perform their role.
Least Privilege
Whereas, least privilege is focused on restricting a user’s actions to only those required for them to perform their role.
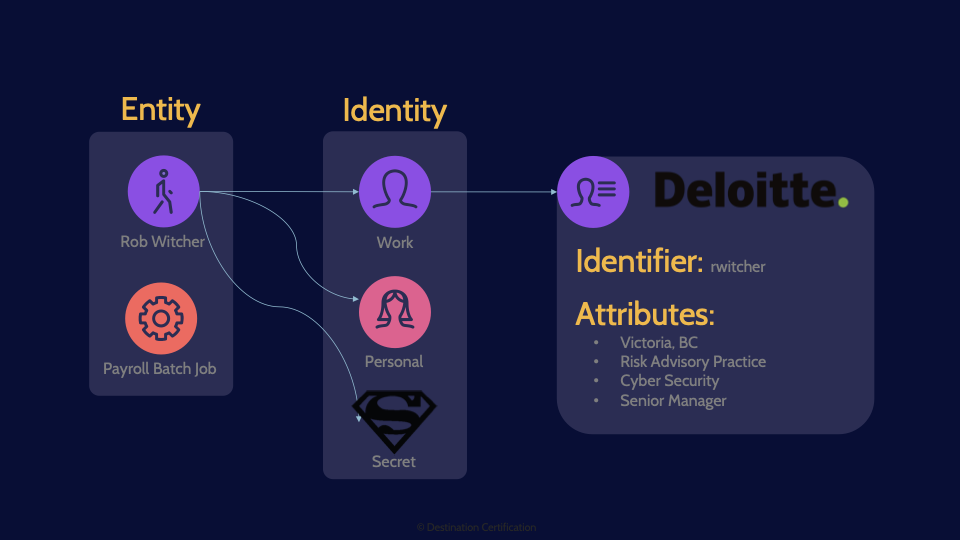
Entity
Now, for some terminology: An entity is a single unique person or process that can have multiple associated Identities.
Identity
Identities vary according to context. So an entity, such as a person, can have multiple identities, such as work and personal.
Identifier
An identifier is a means by which an identity can be asserted, such as a username or an ID card. Identifiers are just how you uniquely identify and specific identity. I’m sure that helped clarify it for you!
Attributes
Attributes are information associated with an identity, such as name, address, role, phone number, etc.

Here’s a diagram that will help you visualize the relationship between all of these. An entity is a person or a process. An entity can have multiple identities. Each identity will have a unique identifier (like a username), plus some attributes (like job role, title, office phone number, email address, etc.).
Access Controls Services
Now, let’s talk about the access controls services. There are four major services that all access control systems must provide: identification, authentication, authorization, and accountability.
Identification
We’ll start with identification. This is where the user must assert their identity to the system. For example, my username is rwitcher.
Authentication
Authentication is where the system verifies the user’s identity via one of the three factors of authentication: knowledge, ownership, or characteristic.
Knowledge
Authentication by knowledge, also referred to as something you know, is where a user verifies their identity by providing some information that they have memorized.
Ownership
The second factor of authentication is ownership, also referred to as something you have. Authentication by ownership is done with things that we have in our possession, such as a hardware security token, or a phone with an authenticator app.
Characteristic
Authentication by characteristic. The reason we call it characteristic and not just biometrics is that there are two main characteristics that we can look at for authentication, physiological and behavioral characteristics. Physiological includes things like your fingerprint or iris scan, while behavioral can be things like your gait or handwriting.
Single / Multifactor
We have now discussed the three factors of authentication: knowledge, ownership and characteristics. Single-factor authentication is simply one of these factors. So if you just log in with a password–that is single-factor authentication. Or if you just access a building by scanning your retina, that is single-factor authentication.
Multi-factor authentication means using two or more different factors of authentication. So logging into a system with your password, and a one-time password from the authenticator app on your phone–that is multifactor authentication. Your password is considered a knowledge factor, while the one-time password from the authenticator app is an ownership factor, because it relies on you having ownership of the specific device.
What about logging in by entering a password and then answering a security question? A password is authentication by knowledge, and answering a security question is also authentication by knowledge–the same factors. So this would be single factor authentication. It’s important to be wary of this mistake.
Authorization
Now, let’s talk about authorization, this is where we define a user’s specific access within a system, what they are authorized to access, and this is where we apply principles like least privilege and need to know.
Accountability
The final and most important access control service is accountability. To have security, we must ensure users are accountable for their actions in a system.
Allows users to access multiple systems with a single set of credentials
We’re now going to talk about two major types of systems that will allow users to access multiple systems with a single set of credentials: Single sign-on and federated identity management. Both allow users to access multiple systems with a single set of credentials. Users love this as they now only need to remember one terrible password instead of multiple terrible passwords, and they only need to authenticate once to magically get access to all their applications.
Single Sign-on (Access systems only within the same organization)
So what’s the difference between single sign-on and federated identity management? Single sign-on systems only allow users to access systems in a single security domain–systems within a single organization. Whereas, as we’ll talk about in a moment, federated identity management protocols allow users to access systems across multiple security domains.
Kerberos
The one major single sign-on protocol that you need to know about is Kerberos. Kerberos enables authentication via tickets over an insecure network, and allows users to access multiple systems while only having to authenticate once.
Federated Access (Access systems across multiple entities)
Federated identity management, as I just mentioned, allows users to access systems across multiple security domains. What does that mean exactly? It means that a user could login to Spotify with their google account. Or authenticate to their corporate Active Directory server (when they login to their laptop) and then access multiple cloud services provided by other companies–without having to log into each cloud service separately. Super convenient!
Federated access relies on a trust relationship between three different entities: the user, the identity provider and the service provider.
Trust Relationship
Essentially, the service provider needs to trust the authentication that is being performed by the identity provider in order to authorize the user to access the service.
Principal / User
Let’s dig into these three entities: The first in the user, sometimes also referred to as the principal.
Identity Provider
The identity provider is the entity that authenticates the user. It verifies the user’s identity via authentication by knowledge, ownership, or characteristic. In many organizations, the identity provider will be something like Active Directory.
Relying Party / Service Provider
The service provider, sometimes also referred to as the relying party, is what the user wants to access. The service provider is often not an application owned by the organization, but rather an application owned and managed by a vendor. Again, think of SaaS applications that so many of us access through work nowadays for submitting helpdesk tickets, booking travel, entering expenses, etc.
SAML
There are a number of different protocols that enable federated access. The major one that you need to know about is SAML–the Security Assertion Markup Language
Tokens
As we talked about, Kerberos relies on sending tickets. SAML does the same thing, but doesn’t call them tickets. Instead, they are called tokens
Assertions written in XML
These tokens contain assertion statements–things like the user ID, the service ID, the timestamp, and lifetime of the token. Assertions statements contained within a token are written in XML–the extensible Markup Language
WS-Federation, OpenID, OAuth
There are three more protocols that you should recognize as federated access protocols. WS-Federation, which provides both authentication and authorization capabilities.
OpenID, which provides authentication.
And OAuth, which provides authorization capabilities.
Privileged User Management
Privileged user management is the practice of carefully managing the permissions of privileged users. Because these users have a greater degree of access than normal, they can also cause more damage, which means that they need to scrutinized more frequently and have any unnecessary permissions removed.
Secrets Management
Secrets management is the practice of appropriately securing high value secrets like passwords and keys over their lifetimes.
CASB
For the final item in this MindMap: A cloud access security broker (CASB) is a security solution that sits between cloud consumers and cloud service providers to enforce security policies and protect data. CASBs provide visibility into cloud service usage, monitor user activity, enforce data security policies, and detect threats. They help with data loss prevention (DLP), encryption, access control, and compliance, ensuring secure use of cloud services across an organization. CASBs enable companies to protect sensitive data, prevent unauthorized access, and ensure cloud usage aligns with corporate and regulatory requirements.

That’s all for this wrapup of access control within Domain 4, covering the essential topics you need to know for the exam.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!