CCSP Domain 6 - Cloud Privacy Issues MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
This is our second and final MindMap for Domain 6, and we're going to be discussing Cloud Audit. Throughout this MindMap, we will be explaining how these ideas interrelate to help guide your studies. This MindMap is just a small fraction of our complete CCSP MasterClass.

This is the second of two videos for Domain 6, which means that it’s also the last video in our CCSP MindMap series. I have included links to the other MindMap videos in the description below. These MindMaps are a limited part of our complete CCSP MasterClass.
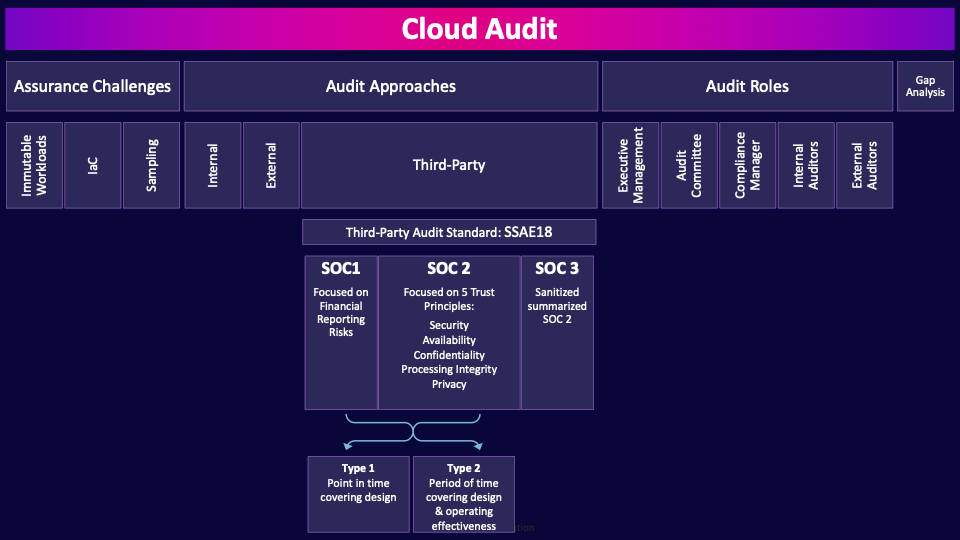
Cloud Audit
Auditing in the cloud is fundamentally different to auditing an on-premises server. Due to the immense complexity of virtualization in the cloud, a system could be spread across hundreds of devices, and perhaps even multiple data centers. Even just a single VM relies on a ton of infrastructure underneath it, and in the public cloud, much of it will be shared with other tenants. Cloud providers generally won’t let you audit their systems, because it would put the privacy of other tenants at risk, so you have to rely on third-party audits.
Assurance Challenges
There are a few other auditing challenges that you need to be aware of.
Immutable Workloads
One challenge is immutable workloads. Auditing immutable workloads requires entirely different test procedures. In a traditional environment, in order to audit, for example, the patching of servers across the organization, you could request an inventory of the servers and then examine a sample of the inventory to see whether they had been patched in a timely manner.
How’s this going to work in the cloud? First, the population of servers is incredibly dynamic in a cloud environment, with VMs constantly being spun up and spun down. When it comes to immutable workloads, these can’t be patched–they are immutable, so it makes no sense to test a sample and ensure that they were patched in a timely manner.
We need to completely change our approach. In the example of patching immutable workloads, you have to test the process for how images are updated and deployed in a timely manner, replacing older unpatched immutable workloads.
It’s a totally different form of testing.
IaC
Auditing infrastructure as code focuses on reviewing code, automated checks, and ensuring consistency throughout the CI/CD processes, which is very different to auditing traditional infrastructure and focusing on manual inspections, live environment checks, and handling configuration drift. The code-driven nature of IaC fundamentally changes how we audit infrastructure, and we need to use very different techniques. However, when it is done correctly there are also potential benefits through early, consistent, and scalable auditing, which makes it more efficient and less error-prone than traditional infrastructure auditing.
Sampling
The traditional auditing technique of asking for a population and then testing a sample of the population is often no longer applicable in the cloud. We often have to move away from sampling. Instead, we need to test the processes that are used. For example, the processes used to update an immutable workload image and ensure that the image is deployed and replaces all the old unpatched workloads.
Jurisdiction
Jurisdiction refers to the authority of a particular court or legal body to hear and decide a case. It’s about "where" or "who" has the power to enforce or interpret the applicable law. For example, a court in British Columbia may have jurisdiction over a case involving parties within its geographic area, even if the applicable law is from another state or country.
Audit Approaches
There are a few different audit approaches that can be employed.
Internal
The first is internal, which is conducted by auditors from the organization on organization processes. The purpose of internal audits is to assess internal controls, risk management, compliance, and operational efficiency. Internal audits help the organization improve processes and identify areas for improvement.
External
The next is external audits, which involve independent auditors from outside the organization, typically from an auditing firm. External audits provide an objective evaluation of compliance with regulations and other requirements. External audits aim to assure stakeholders, such as investors, regulators, and the public, of the organization's accuracy and reliability.
Third-Party
Finally, we have third-party audits, which are conducted by independent third-party organizations (for example, an audit firm like Deloitte) not affiliated with the audited entity–like a cloud service provider. The third-party auditor will conduct the audit of the service provider (much like an external audit)--but the big difference is that the audit results in a report (signed-off by the third-party audit partner) that is given to the service provider, and the service provider can then hand out that report to their customers. This is how customers can get assurance of their cloud service provider’s security controls.
To put it simply, there are three parties involved: the auditor, the service provider, and the service provider’s customers. The auditor conducts the audit and gives their audit report to the service provider, who can then hand out copies of the audit report to its customers.
Unlike internal or external audits, third-party audits are usually specialized in certain compliance or certification areas, providing an objective, unbiased view on the audited entity’s compliance with specific standards or frameworks–such as ISO 27001 or SOC2.
Third-Party Audit Standard: SSAE18
Lets dig into these SOC2 reports. They are super important to understand for the exam.
SSAE 18 stands for Statement of Standards for Attestation Engagements 18, and it's the latest standard for conducting SOC reports. SOC, by the way stands for: System and Organization Controls
SOC1 - Focused on Financial Reporting Risks
There are actually three types of SOC reports. SOC1 reports are focused on financial reporting risks, and these are mainly for financial auditors. As security professionals, they aren’t particularly relevant to us.
SOC 2 - Focused on 5 Trust Principles: Security, Availability, Confidentiality, Processing Integrity, Privacy
SOC 2 reports focus on the 5 trust principles, which are: security, availability, confidentiality, processing integrity, and privacy. The five trust principles are most definitely of interest to us as security professionals!
SOC 3: Sanitized summarized SOC 2
A SOC 3 report is a summarized and sanitized version of a SOC 2 report aimed at public distribution–basically a marketing tool.
Type 1: Point in time covering design
Just to make things a little more confusing, there are two types of SOC1 and SOC2 reports. A Type 1 report looks at the design of a control at a point in time. Essentially reviewing some paperwork on, say, a Monday.
Type 2: Period of time covering design & operating effectiveness
Type 2 reports look at the design and operating effectiveness of a control, over a period of time–typically a year. The auditors are testing to see if a control was operating effectively over a whole year, through sampling and other methods. Type 2 reports are way more useful.
So to sum this up, what we want as security professionals is a SOC 2 Type 2 report.
Audit Roles
Now let’s talk about the different roles that may be involved in the audit and assurance function.
Executive Management
Executive management provides the tone from the top, and promotes and funds the audit process.
Audit Committee
The audit committee is composed of members of the board and senior stakeholders who provide oversight of the audit program.
Compliance Manager
The compliance manager manages the compliance program to ensure corporate compliance with applicable laws and regulations, professional standards, and company policy.
Internal Auditors
Internal auditors are company employees who provide assurance that corporate controls are operating effectively.
External Auditors
External auditors provide unbiased and independent assurance as they are independent of the entity being audited.
Gap Analysis
And here we are, we have arrived at the final box in the final CCSP MindMap!
Gap analysis is basically a comparison of the actual security controls that are in place versus the desired controls. Common standards to compare against are ISO 27001, or the Cloud Controls Matrix. Gap analysis is really important for helping to find your organization’s shortcomings.

And that is an overview of cloud audits within Domain 6, covering some of the most important concepts you need to know for the exam. It also concludes our MindMap series. Hopefully this has helped you understand the connections between the many complex topics of the CCSP exam and will help you prepare to confidently pass the exam.

This is the final MindMap in the series.
My business Partner, John Berti, has been teaching CCSP classes for over 20 years. I’ve been teaching for around 10 years myself. We love helping folks like yourself learn and become better security professionals. Truly what drives us to continue teaching and spending so much time creating the best CCSP study materials is we find it incredibly personally rewarding to guide folks like yourself to achieving your CCSP certification. We get emails all the time from our students saying: I passed! Thank you!
We love these emails.
So I truly hope these MindMap videos have helped you in your studies and help you achieve your CCSP certification.
Thanks very much for watching! And all the best in your studies!