CCSP Domain 4 - Application Security Awareness MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help you pass the CCSP exam. We are going to review the major topics related to cloud development in Domain 4, to guide your studies and show you the links between these concepts.

This is the first of seven videos for Domain 4. I have included links to the other MindMap videos in the description below. These MindMaps are a bite-sized part of our complete CCSP MasterClass.
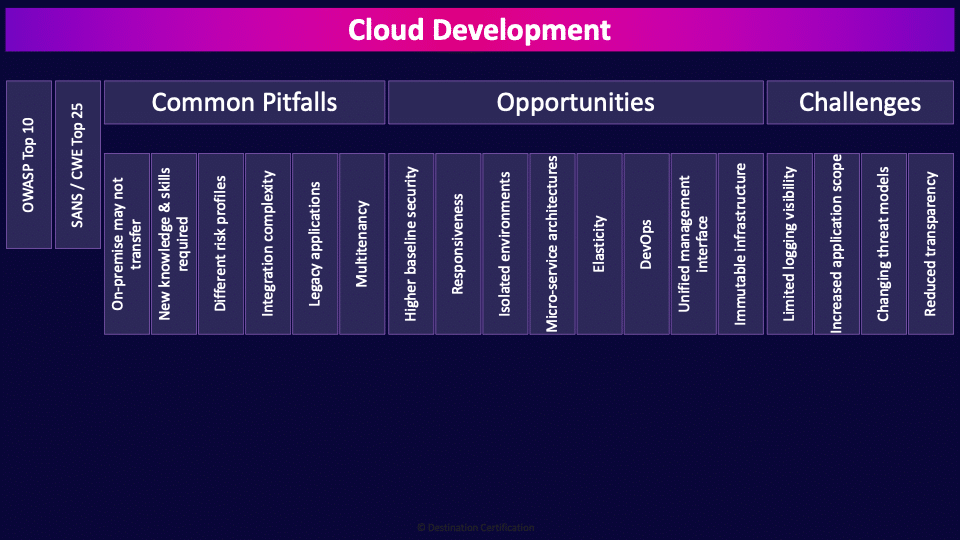
Cloud Development
There are a variety of benefits that come from developing applications in the cloud. For example, you can simply sign up to a PaaS provider and be ready to start coding within minutes, with no need to spend forever setting up and managing your infrastructure. However, there are also a number of pitfalls that come with the cloud, including increased complexity, and new or exacerbated risks.
In this MindMap we’re going to talk through some of the common pitfalls, opportunities and challenges.
We’re going to start with a couple of lists that are important to know about. These lists can help you develop more secure applications.
OWASP Top 10

OWASP is the Open Worldwide Application Security Project, an organization that works to improve software security. One of its projects is the OWASP Top 10, which is a list of the most common web application vulnerabilities that you need to watch out for. The most common vulnerabilities include broken access control, cryptographic failures, and various types of injection, like SQL injection. This is a very useful list. If you are building a web-based application, you had better make sure it’s not vulnerable to the 10 most common vulnerabilities in the world.
SANS / CWE Top 25

Another handy list that you should know about is the CWE TOP 25 Most Dangerous Software Weaknesses, which includes things like Out-of-bounds Write, Cross-site Scripting, and OS command injection. It’s exactly the same idea–when developing an application, ensure it doesn’t have any of the top 25 vulnerabilities from the list. CWE, by the way, stands for Common Weakness Enumeration.
Common Pitfalls
When developing cloud applications there are a range of pitfalls that you need to watch out for. These include:
On-premise may not transfer
Your on-premise systems and development practices may not transfer very well to the cloud. What may have worked well on premise may not work well in the cloud. The cloud has inherently different risks and different controls must be employed to mitigate these risks. In other words you often need to employ different techniques when developing systems in the cloud.
New knowledge & skills required
Developing applications in the cloud requires new knowledge and skills if you want to be able to effectively manage and secure your systems.
Different risk profiles
Cloud also comes with a variety of new risks, including things like compliance challenges. For example, it can be easy to store your data in a location that violates your regulatory requirements. Another big change is that cloud apps are exposed to the Internet, meaning that you can’t bury them deep in your internal network, with layer upon layer of security controls guarding them. This level of exposure means that you really need to take care regarding which security mechanisms you implement, and how you go about it. You often want to employ strategies like zero trust when building systems in the cloud.
Integration complexity
Cloud development often involves a high level of integration from a variety of vendors. For example, you could be using an identity and access service from one provider, a database service from another provider, and so on. When your cloud software is composed of so many different parts, it can be a challenge to integrate them all and keep them functioning appropriately and sufficiently secured.
Legacy applications
Legacy applications can be very difficult to move to the cloud. It’s not uncommon to see lower availability if you migrate the system to a cloud provider than if you kept it on premises. Many legacy systems will either not run in the cloud at all, or not run easily in the cloud.
Multitenancy
Public cloud services are multitenant by nature, which means that many cloud customers are sharing the same underlying physical hardware. They are isolated logically, but there is a chance that this can be implemented poorly, allowing customers to access the data of one another. This is why you shouldn’t use public clouds for highly sensitive data and applications. You need to consider the multitenant nature of the public cloud and ensure you have appropriately identified and mitigated the risks.
Opportunities
Now I don’t want to remotely suggest that developing applications in the cloud is all doom and gloom. The cloud brings about a range of opportunities, including:
Higher baseline security
The major cloud services are huge companies, with big teams of highly skilled security professionals. Because of their scale and range of expertise, it’s much easier for them to provide a higher baseline of security than the average small or medium enterprise. You can take advantage of this higher baseline of security when you build an application in the cloud.
Responsiveness
The cloud brings us a variety of ways that can make our apps more responsive, including rapid elasticity and automatic scaling. It can be relatively easy to make a highly responsive and scalable application.
Isolated environments
Virtual infrastructure can be deployed cheaply and easily, which makes it much simpler to create isolated environments in the cloud. Through microsegmentation, and similar techniques, we can isolate our environments (network segments, instances, storage, etc.) at a very granular level with relative ease, providing a high degree of security.
Micro-service architectures
In contrast to traditional monolithic architectures, microservices allow us to break up our apps into small and independent modular parts. This can make it easier to make changes without breaking the entire app. It can also make it easier to create more resilient and scalable applications. However, it can also add complexity.
Elasticity
The rapid elasticity of cloud services means that they can easily handle demand spikes and scale alongside the needs of your business.
DevOps
DevOps is an approach that involves integrating software development with operations. This allows us to iterate on and release new software at a quicker pace. When we bring security into the picture, we call it DevSecOps. It can potentially be easier to employ a DevOps process in the cloud.
Unified management interface
Clouds are controlled by the management plane, which is a unified management interface. You can control almost all aspects of the cloud through the management plane, which can give you a single pane of glass view into all of your infrastructure, making management much easier. However, the immense power and level of access of the management plane also makes it a huge risk, so it must be carefully secured.
Immutable infrastructure
Immutable infrastructure is infrastructure that can’t be changed. On one hand, this makes it very secure, and very consistent, but it also means that if you need to update it, you must completely replace it with a new image that includes the desired changes. Immutable infrastructure has many benefits, but it also means you must completely change how you manage your infrastructure.
Challenges
Alright, a few more cloud development challenges include:
Limited logging visibility
If you are developing on PaaS or IaaS, you won’t have as much control over the underlying infrastructure compared to developing on top of your own hardware. This limits where you can log, so you may not get the kind of visibility into your infrastructure that you desire.
Increased application scope
One of the downsides of the management plane comes from it having so much access and control. If an attacker manages to compromise it, it’s game over for your application.
Changing threat models
Cloud services face different threats to on-premises systems. If you are moving to the cloud, you need to understand the new threats that may be introduced.
Reduced transparency
When you use a cloud service, you won’t have full visibility into what’s under the hood of the provider. Transparency is particularly low for SaaS, but it improves as you move along the spectrum to PaaS and IaaS. You need to understand that you may no longer have as much visibility when you move to the cloud, so you should have appropriate mitigating controls for this reduced transparency.

That’s all for our overview of cloud development in Domain 4. We touched on some of the most important concepts you need to know for the exam.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!