CCSP Domain 4 - Verified Secure Software MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
This is our fifth MindMap for Domain 4, and we're going to be discussing Cryptographic Services, Cryptography & Key Management. Throughout this MindMap, we will be explaining how these ideas interrelate to help guide your studies. This MindMap is just a small fraction of our complete CCSP MasterClass.

This is the fifth of seven videos for Domain 4. I have included links to the other MindMap videos in the description below. These MindMaps are a small part of our complete CCSP MasterClass.

All right it's finally time for a seriously fun MindMap video on… cryptography!
No seriously, cryptography is super cool and fascinating. It's amazing the number of services and capabilities that cryptography enables that we use every single day and probably don’t even realize it.
Want to store your data in a multitenant environment in the cloud where your data is commingled with other customers, and still ensure your data is properly secured? Cryptography!
Are you using a CDN, replicating and caching large amounts of data across the planet, but still want to ensure the data has integrity? Cryptography can do that for you as well.
Do you want to defensibly destroy your data and render it unrecoverable? Cryptoshredding has you covered.
Cryptography is used pervasively in the cloud and it is an incredibly important tool in our security arsenal.
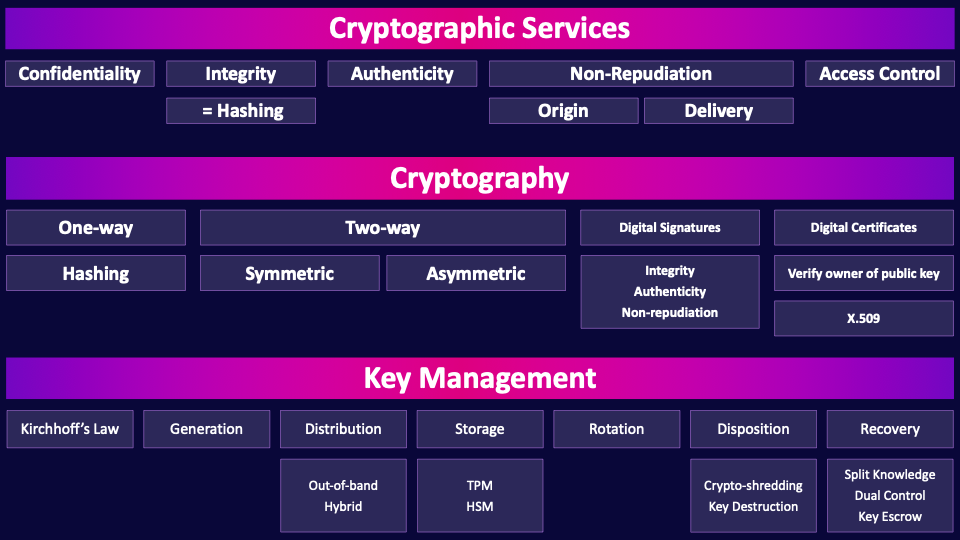
Cryptographic Services
So, let's begin our whirlwind tour of cryptography by talking about the five major services that cryptography provides.
Confidentiality
First up is confidentiality, which allows us to make data available to only those that are authorized to view it–confidentiality helps us to prevent unauthorized disclosure of information.
Integrity
Integrity ensures that information has not been manipulated or changed by unauthorized individuals. Integrity helps us to prevent unauthorized or unexpected changes to data.
Equals Hashing
To achieve integrity we use hashing. So, equate those two in your mind–hashing = integrity | integrity = hashing
Authenticity
Authenticity means we can confirm who something came from, we can for instance verify that a message came from a particular sender.
Non-Repudiation
Non-repudiation prevents someone from denying prior actions. There are two flavors of non-repudiation.
Origin
Non-repudiation of origin means the sender cannot deny that they sent a specific message–they cannot deny the exact message originated from them.
Delivery
Non-repudiation of delivery means the receiver cannot deny that they received a specific message.
Access Control
Finally, cryptography enables a form of access control. By controlling who we give ciphertext to and who we give the decryption key to, we can control who can decrypt and therefore access the data.
Cryptography
Cryptography is the study and application of securing information, generally through techniques like encryption, hashing and digital signatures. Cryptography plays a huge role in the services of confidentiality, integrity, authenticity, non-repudiation and access control. We use encryption for confidentiality, hashing and digital signatures for integrity, and digital signatures for authenticity and non-repudiation.
One-way
There are two ways that we can go about scrambling the letters and turning plaintext into ciphertext. One-way encryption and two-way encryption. One-way encryption means that we turn plaintext into ciphertext, but then we cannot go back in the other direction. We can’t determine what the plaintext was from the ciphertext. Why would we ever want to do such a thing? We use one-way encryption for integrity.
Hashing
We typically call this hashing. Hashing uses one-way mathematical functions which transform an arbitrary length input to a fixed length output–a fixed length message digest. Hashing algorithms need to be deterministic which means the same input will always result in the same output–the same digest. This is how we use hashing for integrity. If you hash the same file over and over again you will always get the same message digest. But if even a single bit in a massive file is changed, then the message digest will be completely different. By hashing a file at different times and comparing the hash values, you can easily see if a file has changed, which allows us to verify integrity.
Two-way
Now let’s talk about two-way encryption which means we can encrypt some plaintext with a key, turning it into ciphertext. As long as we have the right key we can decrypt the ciphertext and turn it back into plaintext. We can encrypt and then later decrypt–we can go in both directions. Two-way.

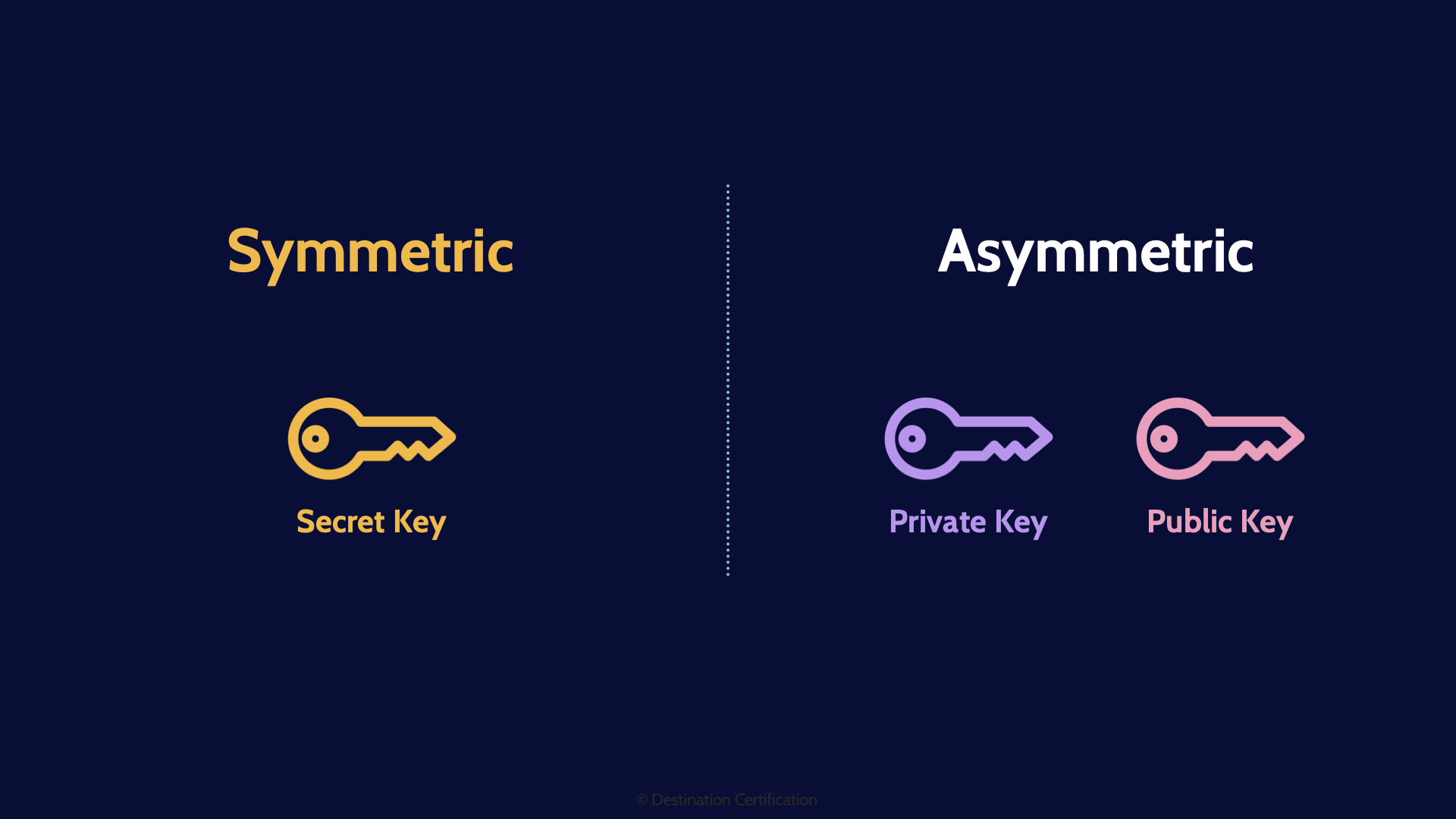
There are two major types of algorithms that we can use to perform two-way encryption: Symmetric algorithms and asymmetric algorithms. The major difference between the two is the number of keys needed to encrypt and decrypt. Symmetric algorithms use just one key to encrypt and the same key to decrypt. Asymmetric algorithms use a keypair. Two keys. One key to encrypt and the other to decrypt–more on asymmetric in a bit.
Symmetric

Symmetric algorithms can be orders of magnitude faster than asymmetric algorithms. So, whenever you need to encrypt lots of data, and encrypt it quickly and efficiently, you need to use symmetric algorithms.
Symmetric algorithms are relatively very fast, efficient, and strong, but they have a major downside: key distribution.
Symmetric cryptography uses the same key to encrypt and the same key to decrypt, which means that if you want to send some data securely you need to encrypt it and send that ciphertext to someone as well as the key they need to decrypt it. I think you can see the problem here. Anyone could intercept the message and get the ciphertext and the key necessary to decrypt it.
To solve this key-distribution problem, you could send the key out-of-band which is often not convenient or efficient–or you can use hybrid cryptography which means you can use asymmetric cryptographic techniques to solve the symmetric key-distribution problem.

Let’s venture into asymmetric algorithms now. The major, seriously cool, and useful, characteristic of asymmetric algorithms is that they use a mathematically related keypair. Two keys.
We give the two keys in the keypair special names and treat them accordingly. We call one key the private key which we must keep absolutely private and not share with anyone ever, under any circumstances. Ever!
And the other key in the key pair, we call the public key, and we give it to anyone and everyone!
Asymmetric
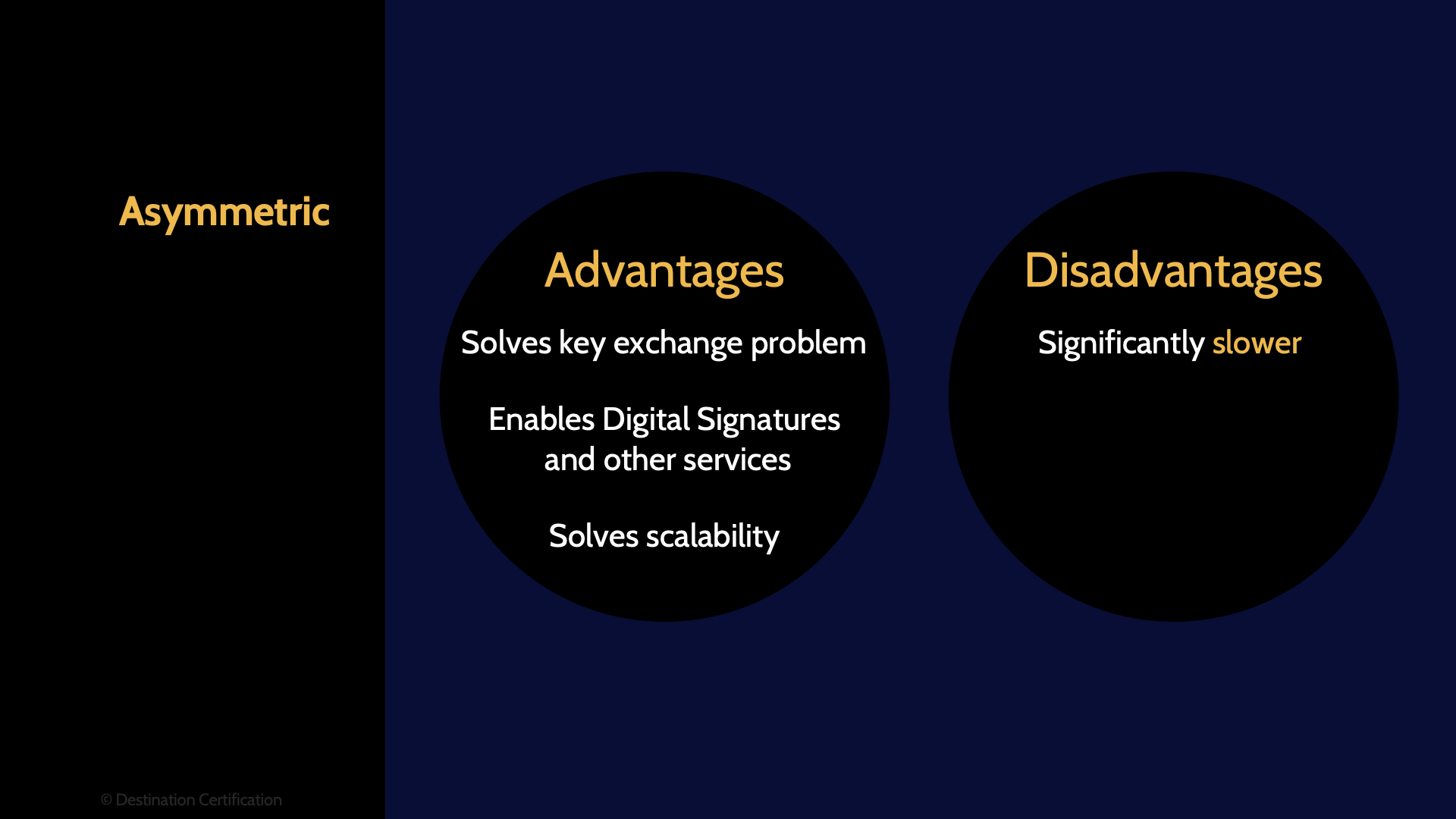
Having this mathematically related keypair enables us to do some seriously useful things. Asymmetric cryptography solves some major issues related to symmetric cryptography: It allows us to securely distribute keys even when we don’t have a pre-existing secure channel, it scales much better than symmetric key encryption, and it allows us to verify integrity, authenticity and non-repudiation when used as part of digital signatures.

We can use asymmetric cryptography to securely and efficiently distribute symmetric keys–solving the key distribution problem.
Not only that, but asymmetric cryptography also enables digital signatures, digital certificates, and the whole root of trust.
Now it’s not all sunshine, rainbows and butterflies with asymmetric cryptography.
It has a major downside. It is slow. Like really slow. It can be orders of magnitude slower than symmetric cryptography. So, whenever we need to encrypt a lot of data, or we need to encrypt as fast as possible, we need to use symmetric cryptography.
Digital Signatures
Digital signatures provide three major and very useful services: Integrity, authenticity and non-repudiation.
We create and use digital signatures in all sorts of different places:
- Sending emails and using digital signatures to verify the integrity, authenticity and non-repudiation of a message.
- Code signing – so that we can verify that an update we just downloaded for our iPhone actually came from Apple and wasn’t modified in transit.
- Signing legal documents, such as PDFs, allowing others to verify who specifically signed the document.
Integrity, Authenticity, Non-repudiation
If someone digitally signs data, we can then verify the signature to determine whether the data has been tampered with, whether it was truly sent by the person who claims to have sent it, and we can also prove whether an individual is responsible for the data. This means that digital signatures give us integrity, authenticity, and non-repudiation.
Digital Certificates
Digital certificates are issued by trusted organizations called certificate authorities.
Verify owner of public key
They allow us to verify the owner of a public key. When you get a certificate, the certificate authority will verify your identity, and then digitally sign your certificate using their private key. Since everyone trusts the certificate authority, they trust that your public key is legitimate, because it has been signed by the certificate authority.
X.509
Digital certificates can be created by many different entities in so many different situations, so we need a standard to make sure all these certificates are interoperable. That standard is X.509.
Key Management
Lets now talk in more detail about keys, and why we need to put so much focus and effort into key management. There is an expression I like: the hardest part of security is cryptography and the hardest part of cryptography is key management. Why is key management so critically important?
Kerckhoffs’ Principle
Auguste Kerckhoffs summed it up nicely in 1883 with his principle: A cryptosystem should be secure even if everything about the system, except the key, is public knowledge. An attacker can know the algorithm being used, the initialization vector, can have access to the ciphertext–the attacker can know all of this and the information will remain secure so long as the key is kept secret.
This obviously implies that we need to do a very good and very secure job of generating keys, distributing keys, storing keys, rotating keys, disposing of keys and even recovering keys.
So, let's talk through each of these key management activities:
Generation
Key generation or key creation is all about creating new symmetric or asymmetric key pairs. What is of critical importance is that each new key must be randomly selected out of the entire keyspace to avoid the plague of cryptography: patterns.
Distribution
Key distribution is focused on securely transmitting shiny new keys to whoever may need them and no one else.
Out-of-band, Hybrid
One method for key distribution is out of band. This involves distributing the key over a previously established secure channel, which could be as simple as securely exchanging it in person. Another option is to use a hybrid model, where we find our recipient’s public key and use it to encrypt the symmetric key. Once the key has been encrypted, we can send it to them, even over an insecure channel. Once they receive it, they can use the private key to decrypt the symmetric key, which then enables them to communicate securely and efficiently with us via the symmetric key.
TPM, HSM
A TPM is a cryptoprocessor that generates and stores keys on endpoints such as laptops.
An HSM is a specific hardware device that is used at the organizational level to securely store and manage keys. HSMs are carefully hardened to keep them secure, because of how valuable the keys are.
Rotation
Key rotation is the concept of changing keys on a periodic basis. If you practice key rotation and a set of keys is compromised, the attacker may only be able to access the data since the last rotation, instead of all of the data. Keys should be rotated as often as necessary. This is dependent on the value of the system, with highly valuable systems requiring keys to be changed more frequently.
Disposition
In the cloud, we generally dispose of our keys through the process of cryptoshredding, because we cannot physically destroy the cloud provider’s hardware.
Crypto-shredding, Key Destruction
Cryptoshredding is a process of purging data by securely encrypting data and then sanitizing all copies of the keys. If all copies of the keys have been securely sanitized, neither ourselves nor attackers can access the data. We use cryptoshredding a lot in the cloud, because we generally can’t destroy the cloud provider’s hard drives.
Recovery
There are a few key recovery mechanisms that you can implement, just in case you lose or accidentally destroy your keys.
Split Knowledge, Dual Control, Key Escrow
The first is split knowledge, which involves dividing a key up between multiple people. To decrypt the data, you need to organize all of the keyholders to input their share of the key. Under certain schemes, you may be able to recover the complete key, even if one person is unavailable.
Another option is dual control. As an example, you could keep secure copies of your organization’s keys in a safe that can only be accessed if two people unlock it at the same time. This keeps the backup keys a little more secure than if they could be accessed by a single authorized person.
FInally, we have key escrow, which involves storing keys with a trusted third-party. If you lose access to your keys, you can get backup copies from the escrow service.

That wraps up our overview of cryptographic services, cryptography and key management for Domain 4. We’ve touched on the important topics you need to know for the exam.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!