CCSP Domain 5 - Operational Controls MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
This is our third and final MindMap for Domain 5, and we're going to be discussing Investigations. Throughout this MindMap, we will be explaining how these ideas interrelate to help guide your studies. This MindMap is just a small fraction of our complete CCSP MasterClass.

This is the third of three videos for Domain 5. I have included links to the other MindMap videos in the description below. These MindMaps are a small part of our complete CCSP MasterClass.
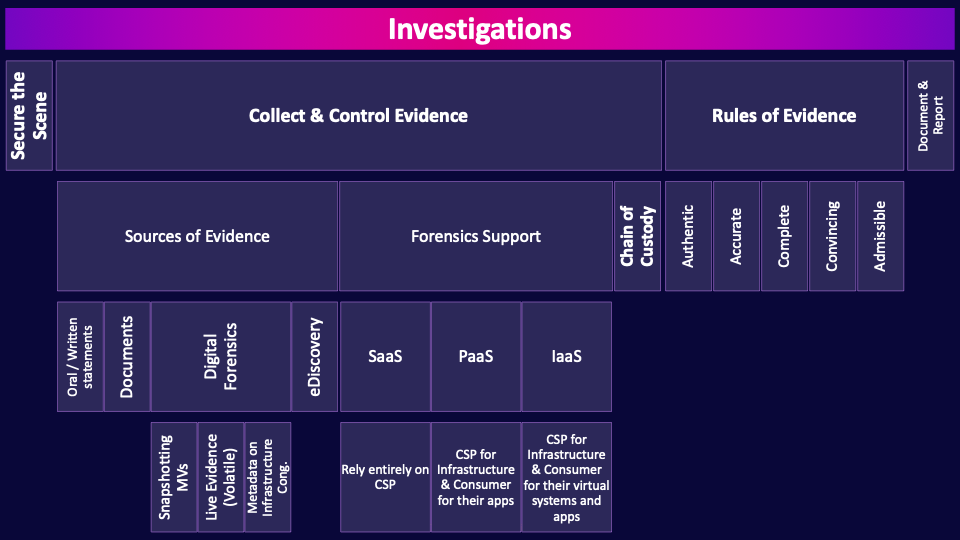
Investigations
Alright, let’s talk about how we apply the principles and methods of forensic science to investigations. This is all about what an organization needs to do if for example they have detected a breach, or had a whistleblower report something, or VISA has called asking why systems are leaking millions of customer credit card numbers.
Secure the Scene
One of the most important first steps is securing the scene. Establishing a perimeter to prevent unauthorized persons from entering the scene in order to avoid the loss, or contamination of evidence. Securing the scene is paramount as once evidence is contaminated it cannot be decontaminated. Securing a digital crime scene is particularly challenging as we want to preserve as much evidence as possible but balance that against things like stopping an ongoing breach. Should a computer system be unplugged from the network or even shut down? Doing so too quickly could compromise the investigation but doing so too slowly could allow additional data to be leaked.
Collect & Control Evidence
Once we begin collecting evidence there are a few principles, techniques and sources we should be aware of.
Sources of Evidence
There are a numerous sources of evidence for an investigator:
Oral / Written statements
Oral or written statements are when witnesses tell an investigator what they witnessed or write it down.
Documents
Documents are any notes, files, etc. that an investigator can find.
Digital Forensics
Digital forensics is the scientific examination and analysis of data from storage media in such a way that the information can be used as evidence in a court of law
Snapshotting VMs
If there has been an incident that needs to be investigated, we can’t just go to the cloud provider and ask them to hand over their hard drives for forensic analysis. Instead, we take snapshots of the VMs, which are essentially copies of the VM, frozen in time. Snapshots are super helpful in digital forensics.
Live Evidence (Volatile)
One of the most challenging and important types of digital evidence is known as live evidence. This is any data stored in volatile memory within a system, such as in RAM or the CPU cache. Recovering live evidence from a physical system requires specialized tools and any live evidence is lost when a system is powered down. Recovering live evidence from a VM is way easier–just take a snapshot.
Metadata on Infrastructure Configuration
As part of a forensic analysis of an incident in the cloud, it may be possible to look at data from the cloud service provider–configuration information such as:
- Instance metadata: types of VMs, including CPU, memory, and storage resources, which could help identify abnormal changes or provisioning.
- Networking metadata: virtual private clouds (VPCs), subnets, routing tables, and network security group rules can indicate potential misconfigurations or unauthorized network changes.
- IAM Metadata: permissions granted to users, roles, and groups.
- Storage, container and encryption key metadata: lots of potential metadata!
Basically, the cloud provider has a ton of information on how the environment is configured and that data can be super useful during an investigation.
eDiscovery
eDiscovery or Electronic Discovery is the process of identifying, collecting and producing electronically stored information for legal proceedings.
ISO 27050
An important international standard to remember related to eDiscovery is ISO 27050. Specifically, ISO 27050 is a set of standards that provides guidelines and best practices for electronic discovery (eDiscovery), covering the identification, collection, and preservation of electronically stored information in legal contexts.
Forensics Support
Forensic investigations can be challenging in the cloud, because you typically have much less control than in on-premises environments. The support that you get from your cloud provider will vary according to the service model.
SaaS
Under the software as a service model, your options are extremely limited.
Rely entirely on CSP
You must rely entirely on the cloud service provider.
PaaS
When it comes to PaaS, you have a little more control.
CSP for Infrastructure & Consumer for their apps
You have to rely on the CSP for the underlying infrastructure, but you are responsible for application logging and any application code you deploy. So, presuming you have built the appropriate capabilities into your application, you may have the data you need for your forensic investigation.
IaaS
Under IaaS, you have the most control, so this is also the service model where you have the most responsibility.
CSP for Infrastructure & Consumer for their virtual systems and apps
You can perform forensic investigations on your virtual system, but you will need the cooperation of your cloud service provider to investigate the underlying infrastructure including network traffic, physical hardware, or to get images of the provider’s hard disks. So a customer has way more ability to perform forensic investigations in the cloud, but they’re still heavily reliant on the CSP.
Chain of Custody
You should associate chain of custody with one word: control. The chain of custody is the process of documenting the complete journey of evidence during the life of the case. Demonstrating control of the evidence–from the moment it was collected to potentially years later when it is presented in a court of law–helps prove that the evidence has integrity.
Rules of Evidence
That leads us to the five rules of evidence which are required for evidence to be considered useful in an investigation.
Authentic
Authentic means you can tie the evidence back to the scene. You can prove the evidence relates to the incident in a relevant way.
Accurate
Accurate equates to integrity–you can prove the evidence has integrity.
Complete
Complete means you collect all evidence, even exculpatory evidence which might help clear a suspect.
Convincing
The evidence must be convincing and reliable and explainable to a jury. Your evidence collection and analysis procedures must not cast doubt on the evidence's authenticity and veracity–its degree of truth.
Admissible
Finally, you want your evidence to be admissible. This is the most basic rule–the evidence must be able to be used in court of law or elsewhere.
Document & Report
The final part of any investigation is the extremely thorough documentation of the evidence collected. The documentation must be prepared to present that evidence to the relevant stakeholders: a judge and jury, the opposition, regulators, investors, etc.

That’s it for our overview of investigations within Domain 5. We’ve covered some of the most important topics to help you with your exam preparations.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!