CCSP Domain 4 - Applying Secure SDLC MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help you pass the CCSP exam. We are going to go through a review of the major topics related to security assessment and testing in Domain 4, to understand how they fit together, which will help to guide your studies.

This is the third of seven videos for Domain 4. I have included links to the other MindMap videos in the description below. These MindMaps are a small part of our complete CCSP MasterClass.
Our systems are becoming ever more complex, we are collecting more data, gathering more insights, rapidly making decisions–these systems are integral to the success of the business.

So what’s the purpose of security assessment and testing?
To ensure that security requirements and controls are defined, tested, and operating effectively to support the business in achieving its goals and objectives.

When should security become involved in testing?
Security assessment and testing covers the gathering and validation of business requirements, the definition of controls, the development of new applications and systems, the ongoing operation, and the eventual retirement and disposal of systems and data.
A good way to summarize this is that testing should be involved right from the start and throughout the process.
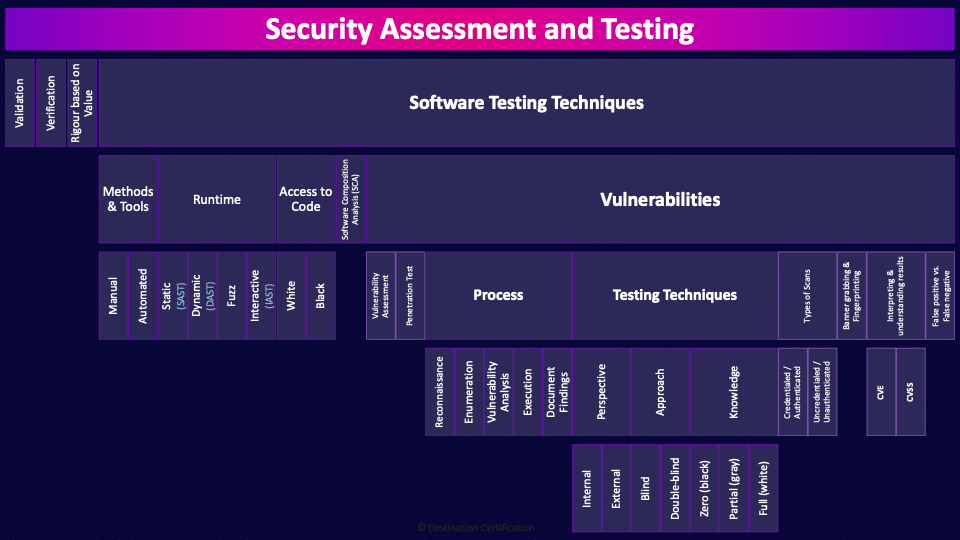
Security Assessment and Testing
In today’s world, no business is going to be successful if they don’t have systems that provide a sufficient degree of confidentiality, integrity and availability. If the systems aren’t working properly and providing the requisite security, the business is being set up for failure. This is why security assessment and testing are so important.
Validation
We’ll start this MindMap with validation. Validation is all about gathering business requirements to truly understand what the business needs are and validating those business requirements with the relevant stakeholders.
Verification
Verification is all the testing we perform once we start designing, architecting and building the product. We are verifying that controls are properly designed and baked into the system.
Rigor based on Value
We can invest very little effort in testing, or we can invest a lot of effort. What drives us to perform more testing to have greater confidence that the system is working correctly? The value of the system to the organization. The more valuable the system, the more effort we will invest in testing to make sure the system is effectively supporting the business in achieving its goals and objectives.
Software Testing Techniques
There are various techniques that we can apply to perform our testing. And note that these techniques can be mixed and matched together to perform different types of tests, they are not mutually exclusive.
Methods & Tools
There are two main methods we can use to perform testing.
Manual
Manual involves hands on the keyboard. A person, manually reading code, or performing some action on a running program.
Automated
Automated implies the use of automated tools–software to test other software. For example code scanning tools, or vulnerability scanners.
Runtime
Runtime is all about whether the code is running or not.
Static (SAST)
Static testing is testing a system that isn’t running. Static testing is looking at code.
Dynamic (DAST)
Dynamic testing means the software is running so you are testing a running system.
Fuzz
Fuzz testing is a form of dynamic testing. It is essentially the idea that programmers are logical people. They expect logical input and provide logical output. If you throw chaos at a system, massive amounts of random data, then you can identify all sorts of unexpected errors and vulnerabilities in the code.
Interactive (IAST)
Interactive application security testing (IAST) involves a combination of both SAST and DAST. Testing is performed as the application is running (DAST) with access to the code (SAST). IAST tools are typically integrated into the software as agents or sensors to monitor the application in real-time.
Access to Code
We can think about testing based upon whether we have access to code.
White
White-box means you have access to the source code for your testing.
Black
Black-box means you can’t see the underlying source code. You are testing a running application and the internal workings are a black box to you.
Software Composition Analysis (SCA)
Software composition analysis is an automated process that identifies open source software in a codebase. It can give us insight into the quality of the code, help us evaluate the security, and check that the licenses are being complied with.
Vulnerabilities
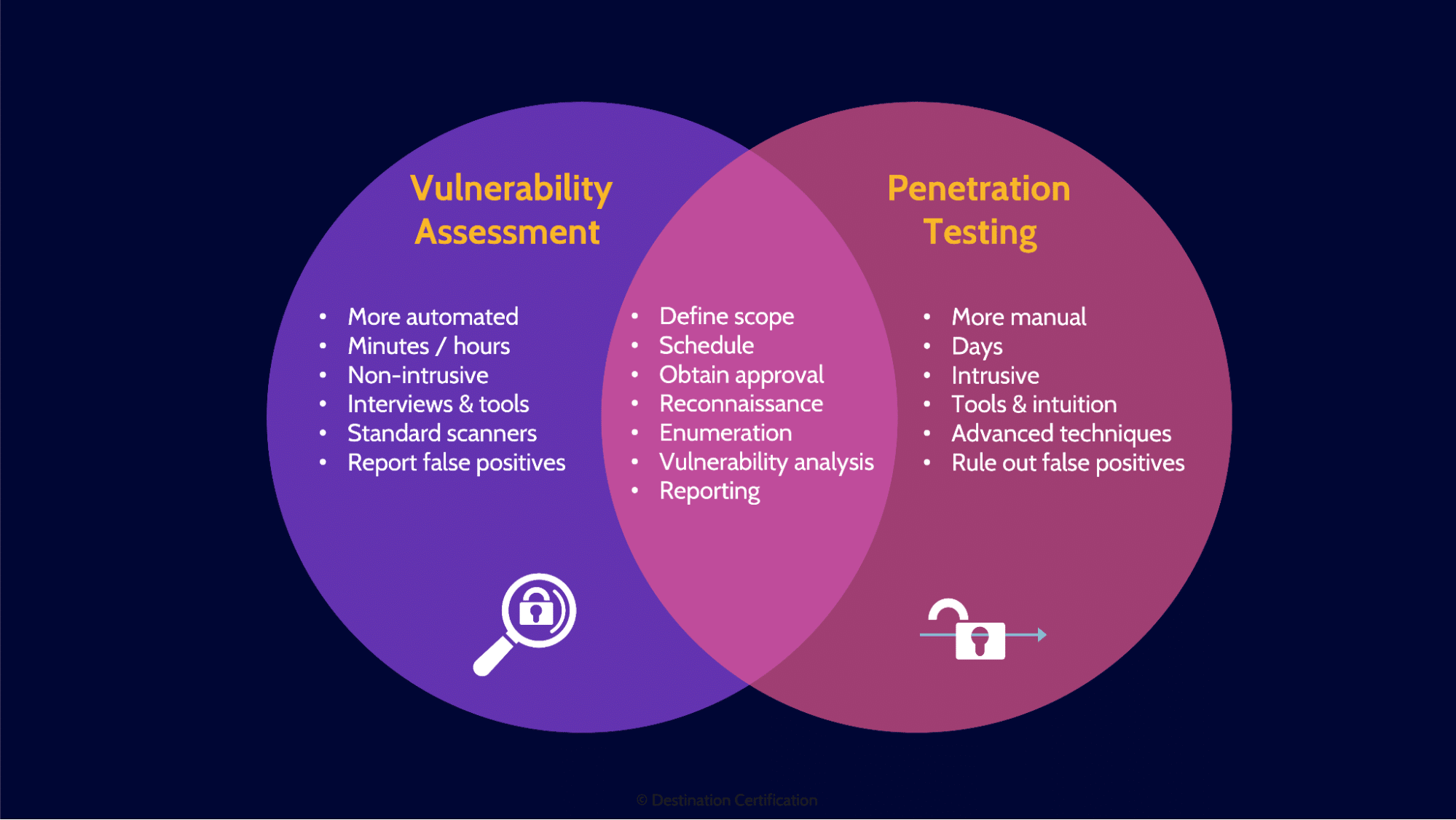
Every system has vulnerabilities. Vulnerability assessment and penetration testing are important parts of testing a system to look for these vulnerabilities: to identify, classify and prioritize remediation.


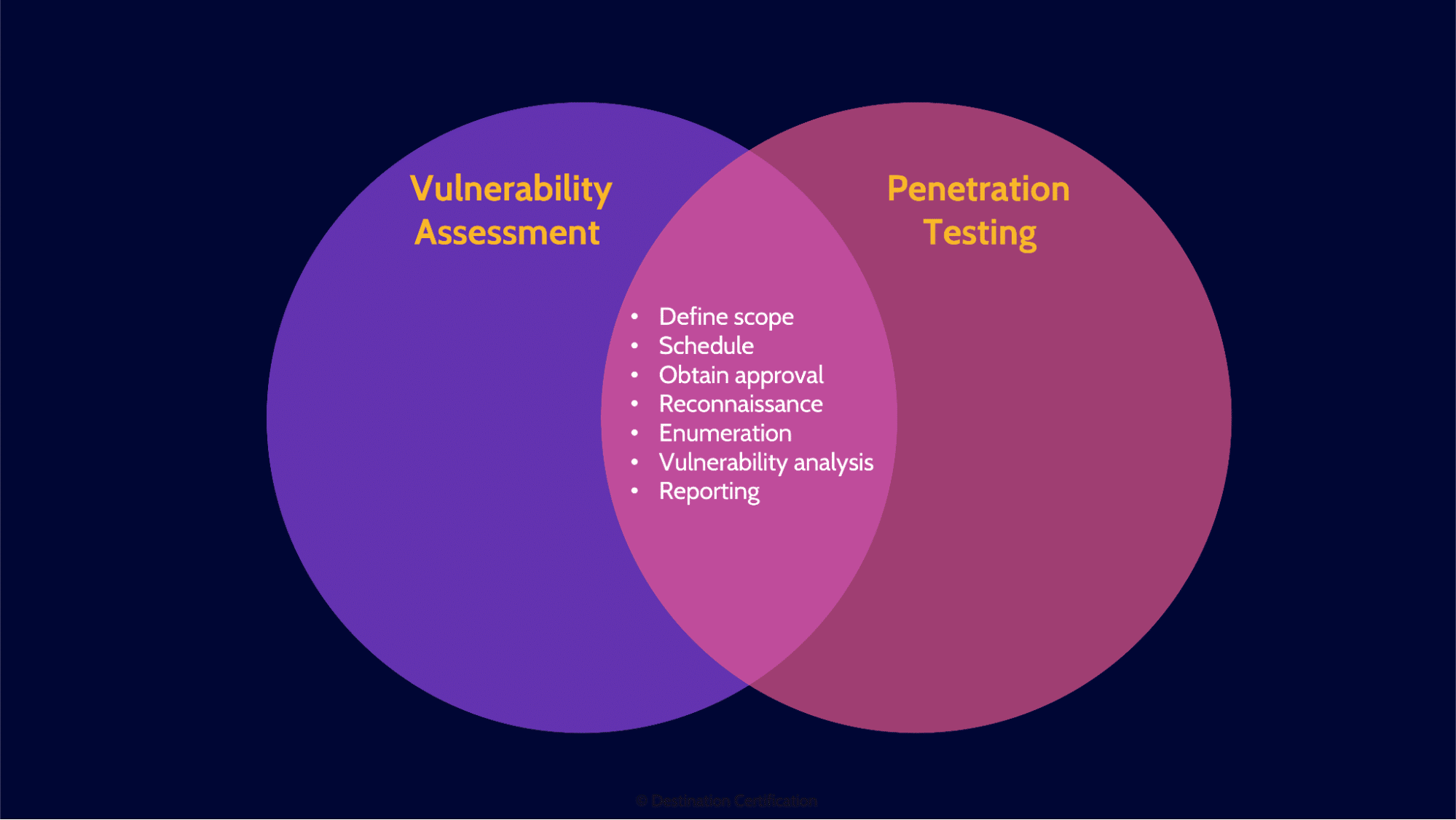
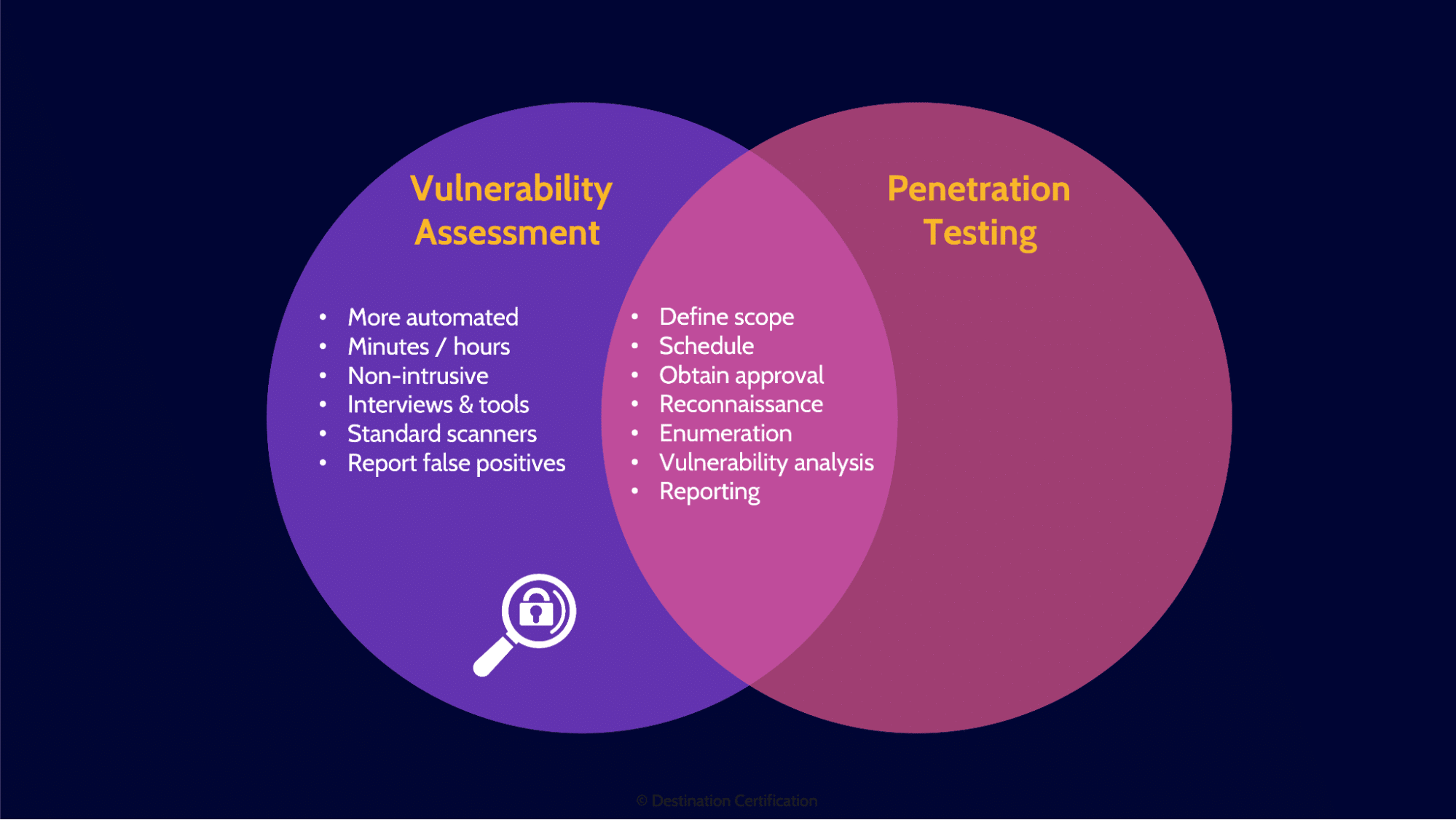
Vulnerability assessments and penetration tests are very similar and start out the same way–identifying potential vulnerabilities and reporting on them to understand the potential impact to the organization, then prioritizing remediation.
Vulnerability Assessment

In a vulnerability assessment once a potential vulnerability has been identified, we skip straight to reporting.
Penetration Test

In a penetration test we identify potential vulnerabilities, and then we attempt to exploit them. This helps us to verify if the vulnerability truly exists and can be exploited, allowing us to eliminate false positives. Vulnerability assessments tend to be faster and more automated but generate far more false positives. Penetration tests are slower and more manual, and have a much higher likelihood of negatively impacting a system, but they provide a much clearer picture of the security of a system.
Process

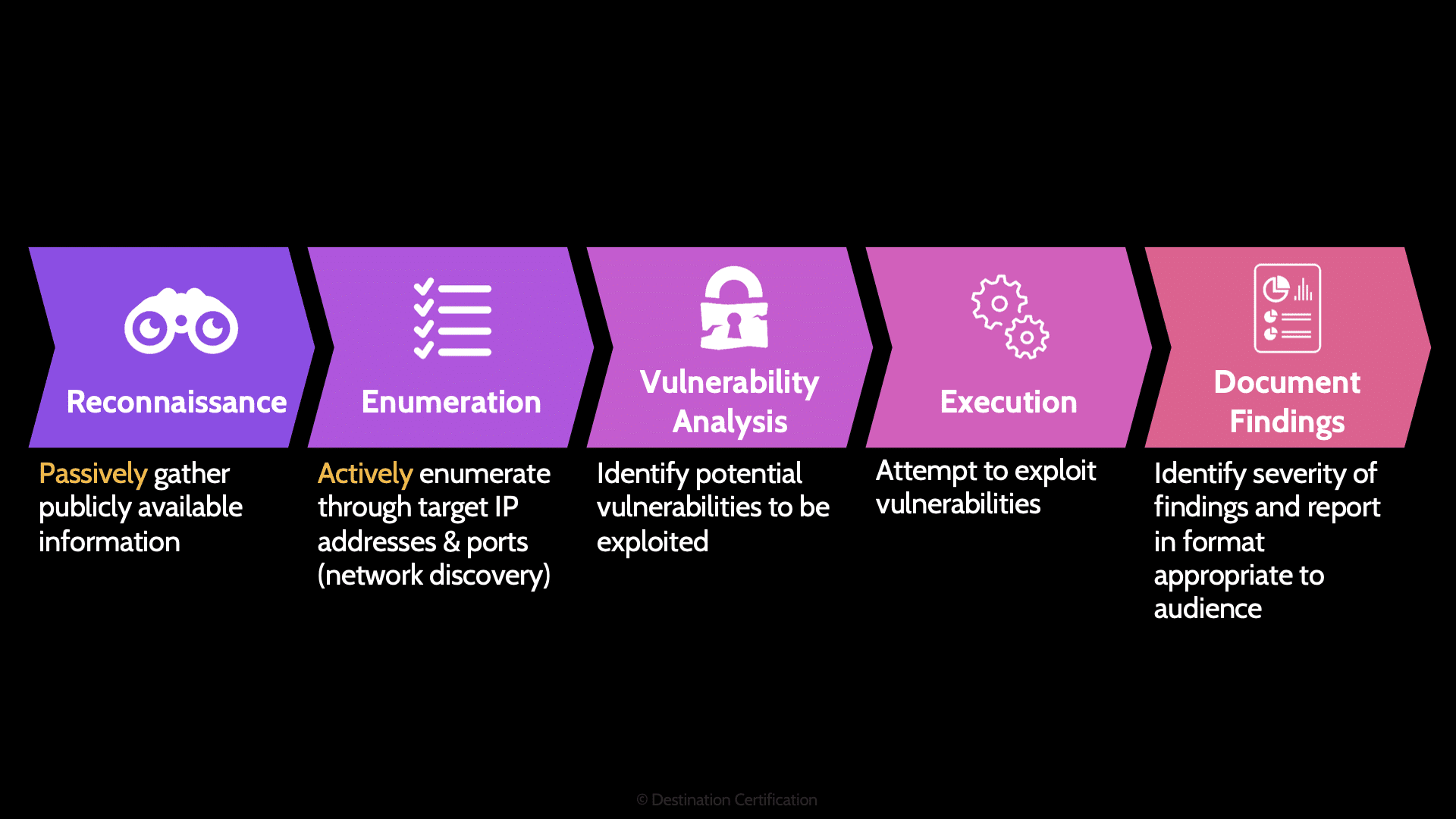
Here is the process we go through to conduct vulnerability assessments and pen tests.
Reconnaissance
We start with reconnaissance, which is a passive activity, the organization being assessed cannot detect anything at this step because the assessor is gathering publicly available information from sources like job postings, LinkedIn profiles, and DNS records.
Enumeration
Enumeration is active, meaning that this step can potentially be detected by the target organization. We are enumerating, systematically walking through IP address ranges and ports to look for live systems that are offering services.
Vulnerability Analysis
Vulnerability analysis is where we determine the exact version of a system and identify potential vulnerabilities that could be exploited. We will talk about how banner grabbing, and fingerprinting can be used to identify the version of a system in a few minutes.
Execution
If we are performing a vulnerability assessment, then we skip execution and go straight to reporting. In a pen test however, the execution step is where we attempt to exploit any vulnerabilities we have identified–we actually break into a system.
Document Findings
Documenting findings is all about reporting on vulnerabilities that have been identified, highlighting the potential impact to the organization, prioritization, and tailoring reports to various audiences.
Testing Techniques
When it comes to testing, there are a wide variety of techniques that can be divided into separate approaches.
Perspective
Perspective is about where the ethical hacker is performing the test from.
Internal
Internal means the testing is performed from within the organization’s network. Simulating the attacker being inside the network.
External
External means the testing is performed from outside the organization's network. Simulating the attacker being outside the firewall, typically out on the Internet.
Approach
Another approach to testing is blind versus double blind.
Blind
Blind testing involves the assessor being given little to no information about the target. However, the target’s IT and security teams will generally know that a test is coming.
Double-blind
Double blind means, not only do we not give the ethical hacker any information, we also don’t tell the organization’s security operations team that the hack is occurring. Double-blind tests not only what the hacker can get into, but also how effectively the organization can detect and respond to the attack.
Knowledge
Knowledge is all about how much information is given to the ethical hacker.
Zero (black)
In zero-knowledge or black-box testing, the tester is given zero knowledge of the system and must rely on publicly available information and whatever they can deduce. This simulates an outsider trying to break in. Zero knowledge and blind tests are the same thing.
Partial (gray)
In partial-knowledge or gray-box testing, the tester is given the knowledge of a user, potentially even elevated privileges on the system, and some basic info on system and network architecture. This makes testing more efficient.
Full (white)
Full-knowledge testing, also known as white-box, open-box or clear-box testing, is where the testers are given full access to source code, full credentials, and detailed architectural documentation. White-box testing is much more focused on going through the source code in detail.
Types of Scans
There are a couple of different types of scans we can perform with vulnerability assessment tools like Nessus or Rapid7.
Credentialed / Authenticated
A credentialed or authenticated scan is where we give the scanning tool the credentials necessary to log into the system or systems being scanned. A credentialed scan can take a deeper look into the exact configuration of a system and thus help eliminate false positives and also help with baseline compliance.
Uncredentialed / Unauthenticated
An uncredentialed scan, as you can probably guess, means we don’t give the scanning tool the credentials necessary to login. This is more of a simulation of an external attacker and what vulnerabilities can be identified from the outside.
Banner grabbing & Fingerprinting
A critical requirement for identifying vulnerabilities is to know the exact version of an operating system and application. Different versions of software are vulnerable to different things. Banner grabbing is where we intentionally get the system to generate something like an error message, like say an error 404 file not found on a web server, and looking at the error message to see if the version number of the system is listed. Systems should be configured not to show this information.
Fingerprinting is far more subtle. By either passively monitoring network traffic going to a system, or actively sending a few specially crafted packets, we can carefully evaluate the exact structure and the contents of packets. Different versions of systems will craft packets in subtly different ways allowing us to fingerprint the exact version.
Interpreting & understanding results
When we run our scans, we need to be able to understand the results. Two instruments that we use are CVEs and CVSSs.
CVE
When different vendors detect a vulnerability for the first time, they often give them their own unique name such as HEARTBLEED. Unfortunately, vendors often come up with their own competing names for the same vulnerability. The role of a CVE number, a Common Vulnerability and Exposure number, is to give each vulnerability a unique but standardized name.
CVSS
The CVSS or Common Vulnerability Scoring System is a standard for assessing the severity of a vulnerability from a zero which means meh, all the way up to 10, which means everyone should be running around screaming.
False positive vs. False negative
False positives occur when you receive an alert, but no incident is taking place. A false negative is when you don’t receive an alert but an incident is taking place. False positives can fatigue your security team, meaning that they may not notice when an actual attack is taking place. It’s best to tune your security tools to minimize false positives. But we don’t want to go too far, to the point that we aren’t being alerted when a true positive occurs, because we won’t know that we are being attacked.

That’s all for our overview of security assessment and testing in Domain 4. We’ve covered the essential topics you need to know for the exam.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!